Hacktivist Campaign Spreads Manifesto through Router Configuration Files

The Black Lotus Labs team at Lumen Technologies recently discovered a hacktivist campaign affecting internet-exposed routers and switches that occurred primarily on May 13, 2021. During this campaign, the threat actor abused the victims’ misconfigured Cisco Smart Install protocol, which was never intended to be exposed to the internet, to remotely alter the router configuration files. While advanced threat actors, as well as hacktivists, previously abused this protocol, the latest iteration caught our attention because of the scope of organizations impacted and disruptive nature of the exploitation.
Technical Details
During an investigation of suspicious third-party router activity, Black Lotus Labs detected potential exploitation of the Smart Install protocol through observing bidirectional connections over TCP port 4786 with SYN/ACK or ACK/PSH flags set and bytes greater than or equal to 53, which indicate a data transfer from the client devices. We also looked for variation in the packet size sent from the attacking IP with fewer established connections, demonstrating targeting – rather than scanning – behavior. By abusing this protocol, the threat actor instructed the exposed router to use TFTP, a common transfer method for router configuration files, to pull down a text file containing a manifesto, stored at the URL: tftp://95.179.251.217.vultr[.]com/my.conf. This installation replaced the existing router configuration, preventing the devices from routing traffic.
Black Lotus Labs’ global visibility suggests targeting for this campaign was opportunistic, as it affected both public sector and private entities. Our visibility indicates the campaign affected at least 100 organizations, with the majority of victims correlated to IPs predominately based in the United States.
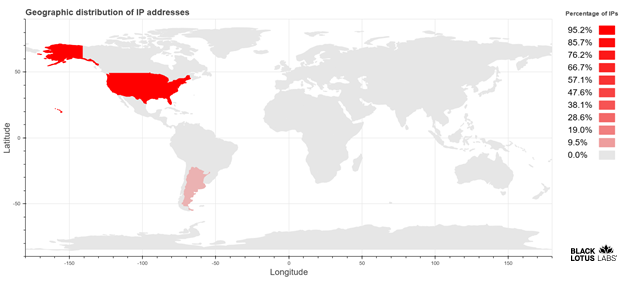
Heatmap of global victim distribution based on IP address
The Cisco Smart Install feature was originally intended to enable a universal plug-and-play capability to eliminate the need to manually configure a device from the command line console. However, it is only meant to be used for internal, or non-internet exposed routers and switches. If this feature is not manually turned off by the network administrator, the device remains vulnerable to this class of attack. In this instance, the threat actor replaced the configuration file with a politically charged anti-Western manifesto copied from a website that allows its userbase to upload stories. In order to avoid amplifying the voice of cybercriminals, we will not copy the text of the message or link to the aforementioned website in this blog.

Snapshot of website hosting hacktivist manifesto
While the hacktivist successfully attacked at least 100 routers, the Smart Install protocol is exposed on over 18,000 internet exposed devices around the world according to ShadowServer, a foundation that is currently scanning for publicly accessible devices that have the Cisco Smart Install service running.
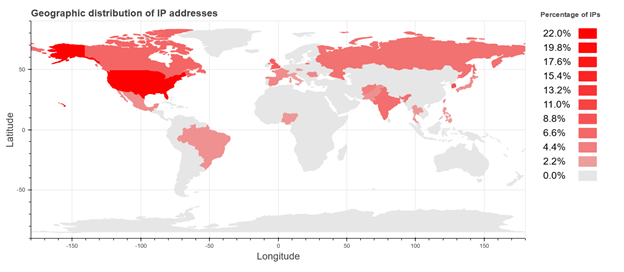
Heatmap of internet-exposed devices with Smart Install protocol, according to ShadowServer
Despite the long history of advanced threat actors and hacktivists abusing the Smart Install protocol, the ongoing exposure of devices continues to be of interest to actors seeking to exploit it. To date in 2021, Black Lotus Labs identified more than 800 unique scanners looking for port 4786.
Mitigation Recommendations
While this type of attack caused some network outages and disruptions, it does not appear to permanently impact the affected devices. To mitigate the attack, victims should remove the threat actor files and rebuild their routing configurations. If you are a network administrator, we recommend you disable this Smart Install feature on all internet-exposed devices. You can verify if your organization has any publicly exposed devices vulnerable to this attack by checking the organization’s footprint with Shadow Server. Additional information about how to secure Cisco routers within your organization is available from Cisco’s Product Security Incident Response Team (PSIRT).
In order to combat this particular campaign, Black Lotus Labs null-routed the IP address (95.179.251[.]21) across the Lumen global network and added it to a block list for Lumen security customers. We will continue to look for threat actors exploiting this protocol.
If you would like to collaborate on similar research, please contact us on Twitter @BlackLotusLabs.
This information is provided “as is” without any warranty or condition of any kind, either express or implied. Use of this information is at the end user’s own risk.




