A New DDoS Reflection Attack: Portmapper; An Early Warning to the Industry

The faster those of us in the security and network operator space can detect a new attack vector, the faster we can come up with ways to slow or stall the growth of that method. To accomplish this, Level 3 monitors threat indicators across our network and looks for trends in attacks that we mitigate for our customers. We are also in a unique position as a global backbone operator to often see multiple stages of the attack, not just the final stage targeting the victim. This allows us to block the attacker and work with any unsuspecting third parties to mitigate risk in the future.
In the last few weeks, we witnessed an alarming trend in both traffic behavior and DDoS methods with the introduction of a new DDoS vector: Portmapper.
Preliminary Impact
Active DDoS reflection attacks have taken a serious toll on both businesses and consumers. Some of the most notorious are the NTP attacks of early 2014 that, at their peak, resulted in attacks amplified to multiple hundreds of gigabits per second in size. The Portmapper vector is the latest method for these types of attack. It already has been used in a number of attacks, with the largest impact to organizations taking place August 10 through 12. These attacks targeted only a subset of verticals, primarily focused on gaming, hosting and Internet infrastructure. Level 3’s Threat Research Labs’ goal is for the industry to use this early warning to help stop or slow any future impacts.
Background
Distributed Denial of Service (DDoS) attacks can cripple a variety of resources on the Internet. It is rare that a week goes by without news of some website or company being impacted by an attack. Different attack methods exist, with volumetric attacks consistently popular due to the significant impact and lack of required sophistication.
In recent years we have seen popularity with a variety of UDP based services, especially DNS, NTP and SSDP. Each has been used to allow attackers to both mask their origin and amplify the bandwidth of their volumetric attacks. As each of these vectors has gained in popularity, security researchers and network operators come together to remove open amplification hosts, track down attackers and even block the attack request altogether.
Among other security bulletins on the topic, the US-CERT maintains an alert at https://www.us-cert.gov/ncas/alerts/TA14-017A that provides more details and lists known vectors.
Portmapper
Portmapper (also referred to as rpcbind, portmap or RPC Portmapper) is a mechanism to which Remote Procedure Call (RPC) services register in order to allow for calls to be made to the Internet. Think of it as a directory service for RPC. When a client is looking to find the appropriate service, the Portmapper is queried to assist. This means, when it is queried, the response size varies wildly depending on which RPC services are operating on the host.
As an example:
$ rpcinfo -T udp -p AAA.BBB.CCC.DDD
program vers proto port
100000 2 tcp 111 portmapper
100000 2 udp 111 portmapper
100003 2 udp 2049 nfs
100003 3 udp 2049 nfs
100003 4 udp 2049 nfs
100003 2 tcp 2049 nfs
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100021 1 udp 32768 nlockmgr
100021 3 udp 32768 nlockmgr
100021 4 udp 32768 nlockmgr
100021 1 tcp 34848 nlockmgr
100021 3 tcp 34848 nlockmgr
100021 4 tcp 34848 nlockmgr
100005 1 udp 751 mountd
100005 1 tcp 754 mountd
100005 2 udp 751 mountd
100005 2 tcp 754 mountd
100005 3 udp 751 mountd
100005 3 tcp 754 mountd
100024 1 udp 32770 status
100024 1 tcp 47090 status
Portmapper can run on both TCP or UDP port 111, with UDP being required for the spoofed request to receive an amplified response.
This particular response was one of the smaller received, with a 68 byte query resulting in a 486 byte response for an amplification factor of 7.1x. On the high end of the spectrum, we have seen responses as large as 1930 bytes for an amplification of 28.4x.
To quantify an average amplification size, we took more than 300 of the top talkers seen across our network and measured the average response size. The result was approximately 1241 bytes (18.3x factor). This number was then compared to the values seen in example DDoS attacks. We found the value to be 1348 bytes (19.8x amplification).
Obviously, these amplification factors are a troubling size when it comes to a DDoS vector.
Query Variation
Level 3 Threat Research Labs referenced the Portmapper query size as a 68 byte IP packet destined for UDP port 111. However, that was the witnessed behavior of a single test machine being used in the analysis. It is important for people looking to filter these types of requests to understand what other query sizes are being seen in the wild. To do that, we look at our network information to see the distribution of packet sizes destined for UDP port 111.
Over the sample time period (late June through mid-August) the breakdown of packet sizes destined for the Portmapper UDP service were:
68 bytes – 36%
78 bytes – 25%
69 bytes – 19%
… all others are non-significant at 1% or smaller
This represents the concerning sized packets for filtering queries to the Portmapper service.
Internet Behavior
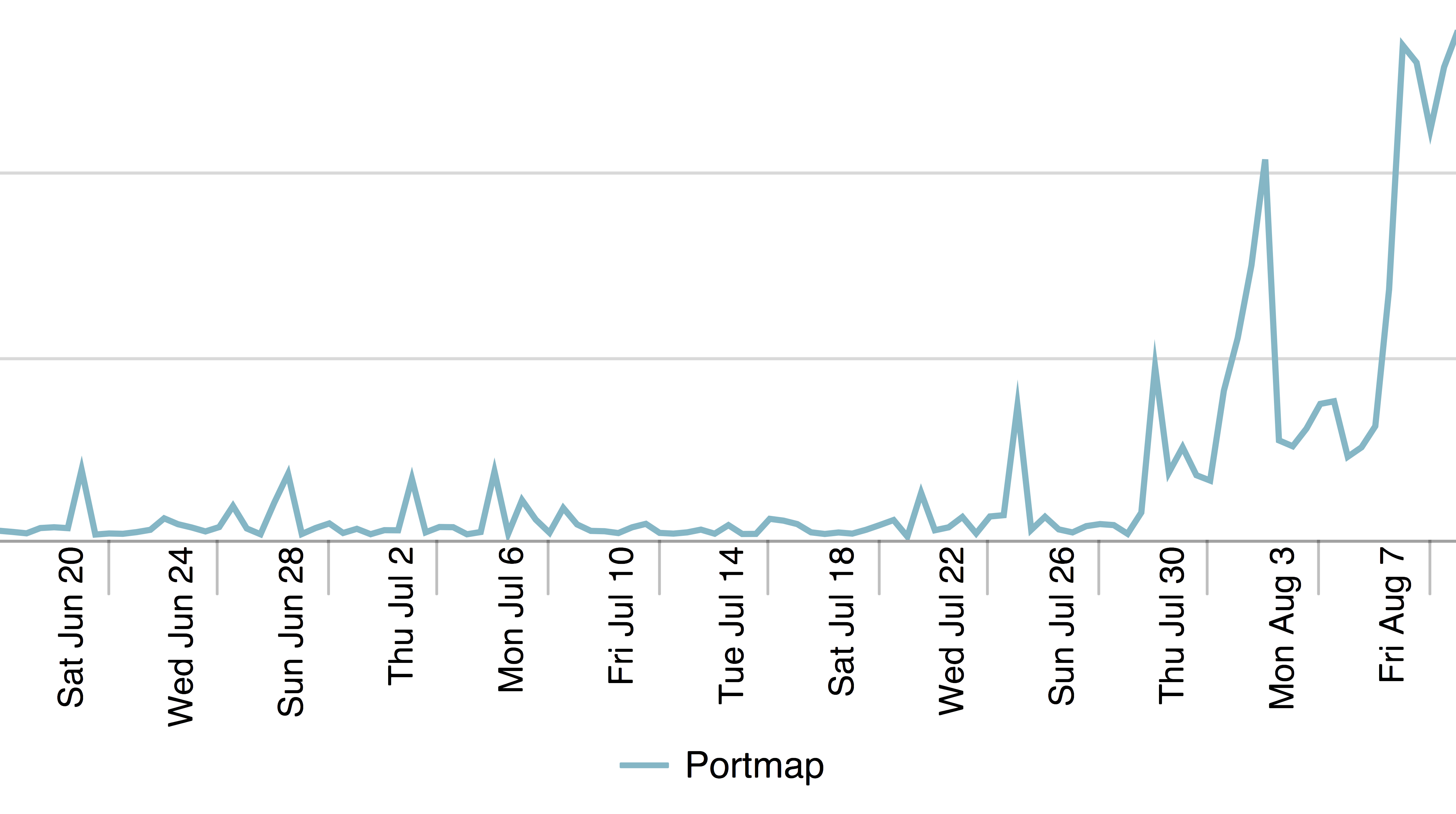
Other reflection attack methods have remained fairly steady in the last few weeks while this particular vector grew substantively.
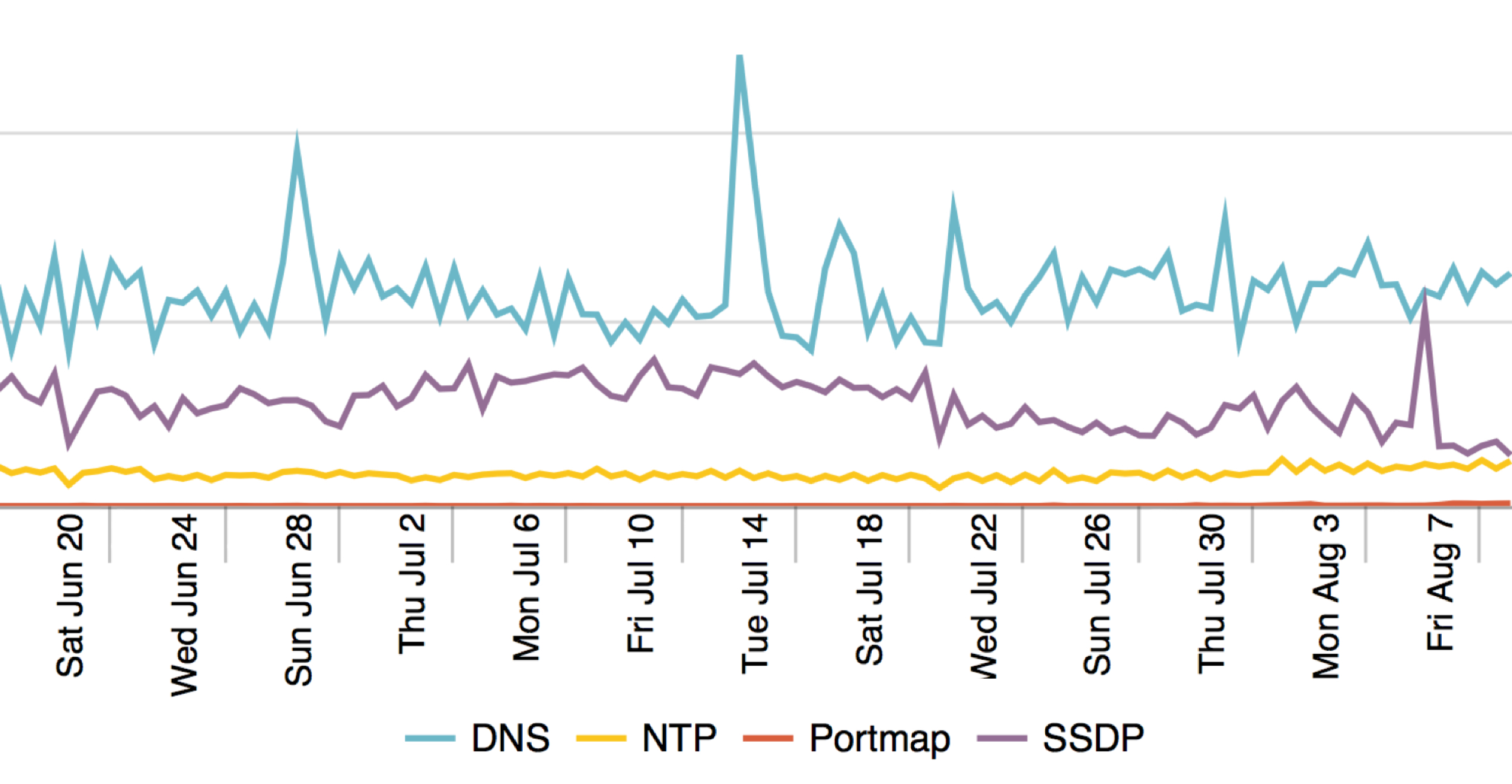
Global portmap traffic grew by a factor of 22x when comparing the last 7 days of June with the 7 days, ending August 12. Clearly the success of using this method for attacks is growing aggressively. However, when Portmapper’s global traffic use is compared with the other popular UDP services, it is clear that the global volume of traffic is still small.
Portmapper is so small it barely registers as the red line at the bottom of the graph. This shows, despite its recent growth, it is a great time to begin filtering requests and removing reflection hosts from the Internet before the attack popularity grows larger and causes more damage.
Recommendations
Portmapper represents a new vector for reflection and amplification DDoS attacks across the Internet. All administrators and organizations should review their continued use of it as an available Internet service in their environment. However, it is not the only vector brought to light here. A number of RPC services on vulnerable hosts are also available on UDP ports. While we have not enumerated each of these directly, they should all be considered a risk to being used for DDoS reflection or amplification. Of course, their very existence on the Internet should be questioned and disabling them considered a best practice.
We recommend disabling Portmapper along with NFS, NIS and all other RPC services across the open Internet as a primary option. In situations where the services must remain live, firewalling which IP addresses can reach said services and, subsequently, switching to TCP-only are mitigations to avoid becoming an unknowing participant in DDoS attacks in the future.
![]()